The Future of Cybersecurity: AI + Zero Trust
CyberShield vison is working to add value in Oman 2040 Vision based on His Majesty Sultan Haitham Bin Tarik below vision. CyberShield OM, a comprehensive cybersecurity solution company designed to safeguard businesses from digital threats with Zero Trust Architects ,Advisory , Products, Implementation and manage services.
"We will not hesitate to exert every effort to achieve the aspirations and objectives we have set in Oman Vision 2040."
Haitham bin Tarik
Sultan of Oman
Key Principles for Zero Trust Architecture 2.0
Zero Trust Architecture (ZTA) 2.0 builds on the foundational principles of Zero Trust but incorporates evolving technologies and modern security challenges. Below are the key principles for ZTA 2.0
Our Services
Collaboration with Singapore and Saudi Arabia Leaders to provide Leader for Products and Services for ZTA
CyberShield Omani Company , collaborates with leading companies in Singapore and Saudi Arabia to mature Zero Trust Architecture. Together, we share knowledge and enhance business security across multiple levels, ensuring robust protection and innovation in cybersecurity.
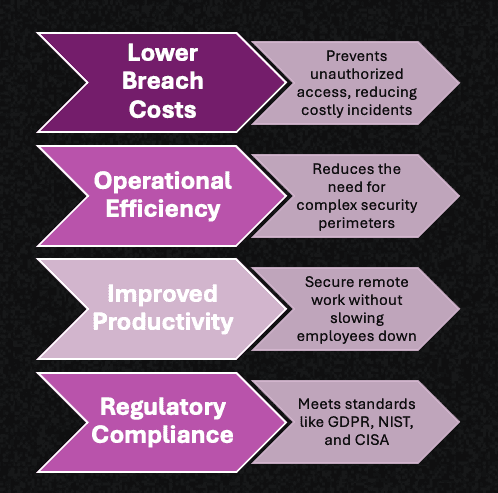
We support how AI and Zero Trust are reshaping the future of cybersecurity, and how to safeguard your organization against evolving threats.Enhance your organization cybersecurity with the latest insights and best practices. We provide the powerful combination of AI and Zero Trust in protecting digital assets and maintaining data integrity.
Customer Success Stories
We are committed to delivering cutting-edge Zero Trust solutions that help businesses enhance security, reduce risks, and ensure compliance. Soon, we will showcase real-world success stories where our expert implementation and industry-leading products have transformed organizations' security postures. Stay tuned for insights on how we help businesses achieve stronger cybersecurity, seamless access management, and proactive threat defense.